Physical Security Incident and Recommend Fixes to Prevent the Incident From Happening Again
Security incidents are events that may indicate that an organization'due south systems or data have been compromised or that measures put in place to protect them have failed.
In IT, a security event is anything that has significance for arrangement hardware or software, and an incident is an event that disrupts normal operations. Security events are usually distinguished from security incidents by the degree of severity and the associated potential risk to the system.
If simply one user is denied access to a requested service, for instance, that may be a security consequence because it could signal a compromised system. Withal, the access failure could too be caused by a number of things. Typically, that one event doesn't accept a severe impact on the organization.
However, if large numbers of users are denied access, it likely means that in that location'southward a more serious problem, such as a deprival-of-service assail, so that effect may be classified as a security incident.
A security alienation is a confirmed incident in which sensitive, confidential or otherwise protected information has been accessed or disclosed in an unauthorized fashion.
Unlike a security breach, a security incident doesn't necessarily mean data has been compromised, only that the data was threatened. For example, an organization that successfully thwarts a cyberattack has experienced a security incident simply non a breach.
How to detect security incidents
Nearly every day in that location's a new headline most one high-profile data breach or another. Merely there are many more incidents that become unnoticed because organizations don't know how to notice them.
Hither are some ways enterprises tin can find security incidents:
- Unusual behavior from privileged user accounts. Any anomalies in the behavior of a privileged user business relationship can indicate that someone is using it to proceeds a foothold into a visitor'due south network.
- Unauthorized insiders trying to access servers and data. Many insiders will test the waters to determine exactly what systems and data they can access. Warning signs include unauthorized users attempting to access servers and information, requesting access to data that isn't related to their jobs, logging in at aberrant times from unusual locations or logging in from multiple locations in a brusque fourth dimension frame.
- Anomalies in outbound network traffic. Information technology'due south not just traffic that comes into a network that organizations should worry near. Organizations should monitor for traffic leaving their perimeters as well. This could include insiders uploading large files to personal deject applications; downloading large files to external storage devices, such as USB flash drives; or sending big numbers of email letters with attachments outside the company.
- Traffic sent to or from unknown locations. For a company that only operates in one country, whatever traffic sent to other countries could bespeak malicious activity. Administrators should investigate any traffic to unknown networks to ensure it'due south legitimate.
- Excessive consumption . An increase in the functioning of server retentiveness or hard drives may mean an attacker is accessing them illegally.
- Changes in configuration. Changes that haven't been canonical, including reconfiguration of services, installation of startup programs or firewall changes, are a sign of possible malicious activity. The same is true of scheduled tasks that have been added.
- Hidden files. These can be considered suspicious because of their file names, sizes or locations, which point the data or logs may have been leaked.
- Unexpected changes. These include user account lockouts, password changes or sudden changes in group memberships.
- Aberrant browsing behavior. This could be unexpected redirects, changes in the browser configuration or repeated popular-ups.
- Suspicious registry entries. This happens mostly when malware infects Windows systems. Information technology's ane of the main ways malware ensures it remains in the infected arrangement.
Common attack vectors
An attack vector is a path or means by which a hacker can proceeds admission to a estimator or network server to evangelize a payload or malicious event. Assault vectors enable hackers to exploit organization vulnerabilities, including human operators.
Assault vectors include viruses, email attachments, webpages, pop-up windows, instant messages, conversation rooms and charade. All of these methods involve programming -- or, in a few cases, hardware. The exception is charade, which is when a man operator is fooled into removing or weakening system defenses.
Although organizations should exist able to handle whatever incident, they should focus on handling incidents that utilize mutual attack vectors. These include the post-obit:
- External/removable media. The set on is executed from removable media -- e.g., CD, wink drive or a peripheral device.
- Attrition. This type of attack uses brute-forcefulness methods to compromise, degrade or destroy networks, systems or services.
- Web. The attack is executed from a website or spider web-based awarding.
- Email. The attack is executed via an e-mail bulletin or attachment to an email. A hacker entices the recipient to either click on a link that takes him to an infected website or to open an infected attachment.
- Improper usage. This blazon of incident stems from the violation of an organization's acceptable-use policies by an authorized user.
- Drive-by downloads. A user views a website that triggers a malware download; this tin can happen without the user's noesis. Drive-by downloads, which take advantage of vulnerabilities in spider web browsers, inject malicious code using JavaScript and other browsing features.
- Advertisement-based malware (malvertising). The attack is executed via malware embedded in advertisements on websites. Simply viewing a malicious ad could inject malicious lawmaking into an unsecured device. In add-on, malicious ads tin too be embedded directly into otherwise trusted apps and served via them.
- Mouse hovering. This takes advantage of vulnerabilities in well-known software, such equally PowerPoint. When a user hovers over a link -- rather than clicking on it -- to see where it goes, beat out scripts can exist launched automatically. Mouse hovering takes advantage of system flaws that make it possible to launch programs based on innocent deportment of the user.
- Scareware. This persuades a user to purchase and download unwanted and potentially dangerous software by scaring him. Scareware tricks a user into thinking that his computer has a virus, then recommends that he download and pay for fake antivirus software to remove the virus. Withal, if the user downloads the software and allows the program to execute, his systems will be infected with malware.
Understanding the attackers methodology and goals
Although an organization can never be sure which path an aggressor will take through its network, hackers typically use a certain methodology -- i.e., a sequence of stages to infiltrate a network and steal data. Each stage indicates a certain goal along the attacker's path. This security industry-accepted methodology, dubbed the Cyber Kill Chain, was developed past Lockheed Martin Corp.
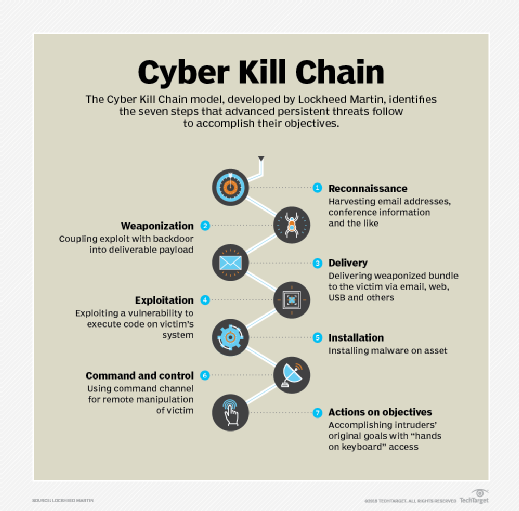
According to Lockheed Martin, these are the stages of an attack:
- Reconnaissance (identify the targets) . The threat actor assesses the targets from outside the organisation to identify the targets that will enable him to run into his objectives. The goal of the attacker is to find data systems with few protections or with vulnerabilities that he can exploit to access the target organisation.
- Weaponization (prepare the operation). During this phase, the attacker creates malware designed specifically for the vulnerabilities discovered during the reconnaissance stage. Based on the intelligence gathered in that stage, the attacker customizes his tool set to run into the specific requirements of the target network.
- Delivery (launch the functioning). The attacker sends the malware to the target past any intrusion method, such as a phishing email, a man-in-the-middle assault or a watering pigsty attack.
- Exploitation (gain admission to victim). The threat actor exploits a vulnerability to gain access to the target's network.
- Installation (constitute beachhead at the victim). Once the hacker has infiltrated the network, he installs a persistent backstairs or implant to maintain admission for an extended period of time.
- Command and control (remotely control the implants). The malware opens a control channel, enabling the assaulter to remotely manipulate the target's systems and devices through the network. The hacker tin can then take over the control of the unabridged affected systems from its administrator.
- Deportment on objectives (achieve the mission'southward goals). What happens side by side, now that the attacker has the control and control of the target's system, is entirely up to the assailant, who may corrupt or steal data, destroy systems or need ransom, among other things.
Mitigate the risk of the 10 mutual security incident types
In that location are many types of cybersecurity incidents that could result in intrusions on an organization's network:
ane. Unauthorized attempts to access systems or data
To foreclose a threat histrion from gaining access to systems or data using an authorized user'due south account, implement 2-factor authentication. This requires a user to provide a 2d slice of identifying information in addition to a password. Additionally, encrypt sensitive corporate data at rest or as information technology travels over a network using suitable software or hardware technology. That way, attackers won't be able to access confidential data.
2. Privilege escalation set on
An attacker who attempts to gain unauthorized admission to an arrangement's network may then try to obtain college-level privileges using what's known equally a privilege escalation exploit. Successful privilege escalation attacks grant threat actors privileges that normal users don't have.
Typically, privilege escalation occurs when the threat actor takes advantage of a issues, configuration oversight and programming errors, or whatever vulnerability in an awarding or system to proceeds elevated admission to protected data.
This usually occurs subsequently a hacker has already compromised a network by gaining access to a low-level user account and is looking to gain college-level privileges -- i.due east., full access to an enterprise's Information technology organisation -- either to written report the arrangement farther or perform an attack.
To decrease the risk of privilege escalation, organizations should look for and remediate security weak spots in their IT environments on a regular basis. They should besides follow the principle of to the lowest degree privilege -- that is, limit the access rights for users to the blank minimum permissions they need to do their jobs -- and implement security monitoring. Organizations should also evaluate the risks to their sensitive data and take the necessary steps to secure that data.
three. Insider threat
This is a malicious or accidental threat to an organization's security or data typically attributed to employees, old employees or tertiary parties, including contractors, temporary workers or customers.
To detect and prevent insider threats, implement spyware scanning programs, antivirus programs, firewalls and a rigorous data backup and archiving routine. In improver, train employees and contractors on security awareness before allowing them to admission the corporate network. Implement employee monitoring software to reduce the risk of information breaches and the theft of intellectual belongings by identifying devil-may-care, disgruntled or malicious insiders.
4. Phishing attack
In a phishing attack, an attacker masquerades as a reputable entity or person in an e-mail or other advice channel. The attacker uses phishing emails to distribute malicious links or attachments that tin can perform a variety of functions, including extracting login credentials or account information from victims. A more targeted blazon of phishing attack known every bit spear phishing occurs when the aggressor invests time researching the victim to pull off an even more than successful set on.
Constructive defence against phishing attacks starts with educating users to identify phishing messages. In add-on, a gateway e-mail filter tin can trap many mass-targeted phishing emails and reduce the number of phishing emails that achieve users' inboxes.
5. Malware set on
This is a broad term for unlike types of malicious software (malware) that are installed on an enterprise'south system. Malware includes Trojans, worms, ransomware, adware, spyware and diverse types of viruses. Some malware is inadvertently installed when an employee clicks on an ad, visits an infected website or installs freeware or other software.
Signs of malware include unusual system activity, such every bit a sudden loss of disk space; unusually slow speeds; repeated crashes or freezes; an increase in unwanted net activeness; and pop-up advertisements. Installing an antivirus tool can detect and remove malware. These tools can either provide real-time protection or detect and remove malware by executing routine organisation scans.
half dozen. Denial-of-service (DoS) attack
A threat actor launches a DoS attack to shut down an individual machine or an entire network so that it's unable to respond to service requests. DoS attacks practise this by flooding the target with traffic or sending it some information that triggers a crash.
An organization tin can typically deal with an DoS attack that crashes a server by simply rebooting the organization. In improver, reconfiguring firewalls, routers and servers can block whatever bogus traffic. Proceed routers and firewalls updated with the latest security patches.
As well, application front end-end hardware that'southward integrated into the network can aid analyze and screen data packets -- i.e., classify data as priority, regular or dangerous -- as they enter the arrangement. The hardware can also help block threatening data.
7. Man-in-the-middle (MitM) attack
A man-in-the-heart attack is one in which the aggressor secretly intercepts and alters messages betwixt two parties who believe they are communicating direct with each other. In this attack, the aggressor manipulates both victims to gain admission to data. Examples of MitM attacks include session hijacking, electronic mail hijacking and Wi-Fi eavesdropping.
Although it's difficult to detect MitM attacks, at that place are ways to prevent them. 1 way is to implement an encryption protocol, such as TLS (Transport Layer Security), that provides authentication, privacy and data integrity between two communicating computer applications. Another encryption protocol is SSH, a network protocol that gives users, particularly system administrators, a secure way to access a figurer over an unsecured network.
Enterprises should besides brainwash employees to the dangers of using open public Wi-Fi, as it's easier for hackers to hack these connections. Organizations should also tell their workers non to pay attention to warnings from browsers that sites or connections may not be legitimate. Companies should as well use VPNs to assist ensure secure connections.
8. Password set on
This blazon of attack is aimed specifically at obtaining a user's password or an business relationship's password. To do this, hackers use a multifariousness of methods, including password-cracking programs, lexicon attack, countersign sniffers or guessing passwords via beast force (trial and error).
A password cracker is an application program used to identify an unknown or forgotten countersign to a calculator or network resources. This helps an assailant obtain unauthorized access to resources. A dictionary set on is a method of breaking into a countersign-protected computer or server by systematically entering every word in a dictionary equally a countersign.
To handle countersign attacks, organizations should adopt multifactor authentication for user validation. In addition, users should use potent passwords that include at least seven characters too as a mix of upper and lowercase letters, numbers and symbols. Users should change their passwords regularly and use different passwords for different accounts. In improver, organizations should use encryption on any passwords stored in secure repositories.
9. Web application assail
This is any incident in which a web application is the vector of the attack, including exploits of code-level vulnerabilities in the application also as thwarting authentication mechanisms. I instance of a spider web application attack is a cross-site scripting attack. This is a type of injection security attack in which an attacker injects information, such every bit a malicious script, into content from otherwise trusted websites.
Enterprises should review code early on in the development stage to detect vulnerabilities; static and dynamic lawmaking scanners can automatically bank check for these. Also, implement bot detection functionality to prevent bots from accessing application data. And a web awarding firewall can monitor a network and block potential attacks.
10. Advanced persistent threat (APT)
An APT is a prolonged and targeted cyberattack typically executed by cybercriminals or nation-states. In this attack, the intruder gains admission to a network and remains undetected for an extended period of fourth dimension. The APT's goal is usually to monitor network activity and steal information rather than crusade damage to the network or organization.
Monitoring incoming and outgoing traffic tin assist organizations prevent hackers from installing backdoors and extracting sensitive data. Enterprises should as well install spider web application firewalls at the edge of their networks to filter traffic coming into their web awarding servers. This can help filter out application layer attacks, such equally SQL injection attacks, oftentimes used during the APT infiltration phase. Additionally, a network firewall tin monitor internal traffic.
Examples of security incidents
Here are several examples of well-known security incidents.
Cybersecurity researchers start detected the Stuxnet worm, used to attack Iran'southward nuclear program, in 2010. It is still considered to be 1 of the nigh sophisticated pieces of malware ever detected. The malware targeted supervisory control and information conquering systems and was spread with infected USB devices. Both the U.South. and Israel accept been linked to the development of Stuxnet, and while neither nation has officially acknowledged its role in developing it, there accept been unofficial confirmations that they were responsible for it.
In October 2016, another major security incident occurred when cybercriminals launched a distributed DoS assail on domain proper noun organization provider Dyn, which disrupted online services worldwide. The assault hit a number of websites, including Netflix, Twitter, PayPal, Pinterest and the PlayStation Network.
In July 2017, a massive breach was discovered involving xiv meg Verizon Communications Inc. client records, including phone numbers and account PINs, which were reportedly exposed to the internet, although Verizon claimed no data was stolen. A month earlier, a researcher from security house UpGuard institute the data on a deject server maintained by data analytics firm Prissy Systems. The information wasn't password protected, and as such, cybercriminals could have been easily downloaded and exploited it, according to the security firm.
Trends in the causes of incidents
According to the 2019 "Data Security Incident Response Report" by BakerHostetler LLP, a U.S. constabulary business firm, certain types of security incidents are on the rise.
Phishing is still the leading cause of security incidents. Nearly i-quarter of all the incidents BakerHostetler responded to in 2018 resulted from lost devices, inadvertent disclosures or arrangement misconfigurations. Employees were responsible for 55% of the 750 incidents the firm responded to in 2018, partly due to simple mistakes and falling for phishing scams. Increasing employee awareness and implementing multifactor authentication are notwithstanding two of the best defenses to accost the employee risk factor, the study noted.
On the bright side, organizations keep to improve their in-house detection capabilities. In 2018, 74% of incidents were detected internally, an increase from only 52% in 2015. Notwithstanding, although more companies have invested in security tools to help investigate security incidents, few organizations accept the experience and chapters to investigate security incidents without third-party help.
Attacks by nation-states are increasing. Nation-states continue to engage in cyberoperations to support espionage, economic development (via the thefts of intellectual property and trade secrets) or demolition. And it has become more than difficult to differentiate between the methods and procedures used by nation-country actors and criminal actors. The reason: It's hard to find expert data on how frequently these attacks occur, in part because they go undetected or unreported.
Creating an incident response program
The expanding threat landscape puts organizations at more risk of existence attacked than always earlier. Every bit a result, enterprises must constantly monitor the threat mural and be ready to respond to security incidents, data breaches and cyberthreats when they occur. Putting a well-defined incident response program in place and taking into consideration some of the tips provided in this study, will enable organizations to effectively identify these incidents, minimize the damage and reduce the cost of a cyberattack. Such a programme will too help companies foreclose future attacks.
This was final published in June 2019
Source: https://www.techtarget.com/searchsecurity/feature/10-types-of-security-incidents-and-how-to-handle-them
0 Response to "Physical Security Incident and Recommend Fixes to Prevent the Incident From Happening Again"
Post a Comment